CLOUD SECURITY
Our digital systems integration infrastructure works amazingly with developing a cloud computing system. Your business growth determines your success story that leads to new evolutions and amazing potential. We can assist with things like maintenance, solution deployment, transformation strategies, and many others. Our team is also ready to assist with SaaS project customization, deployment, and localization, data migration, security, and custom app designs. The cloud provider will handle different aspects of physical infrastructure and the security of applications. Meanwhile, the client will be responsible for the authorization and control of the cloud environment.
Security Responsibilities for Client/Provider
In cloud security, the responsibility to secure the cloud lies on both the client and provider. That’s why it is said to be a shared responsibility. However, shared responsibility doesn’t mean that responsibility becomes less. The cloud provider will handle different aspects of physical infrastructure and the security of applications. Meanwhile, the client will be responsible for the authorization and control of the cloud environment.
DO BUSINESS WITH US!
In order to acquire our services, send us your inquiry of interest. We shall revert immediately.
MOBILE SECURITY
With Alliance Global Tech Inc., you can have access to the best software engineering and application management services. We collaborate on tools for big data to help in delivering amazing results on any device. We professionally custom-build apps with stellar security, scalability, and interoperability features. Our mature application development process covers the entire SDLC and offers a settled environment and framework.
Mobile Security Architecture
OUR IMPLEMENTATIONS
To make the security architecture important, there are certain components that are involved in the design. The components are people, process, and tools. All these components combine to help protect the organization’s assets. After defining the components, the next step is to make the policy and the reinforcement technique for the policies. After the other important steps, the method procedure for the implementation of the security architecture and how the architecture will be enforced. By this, the overall design and architecture are designed for the organization that will protect them throughout their business operations.
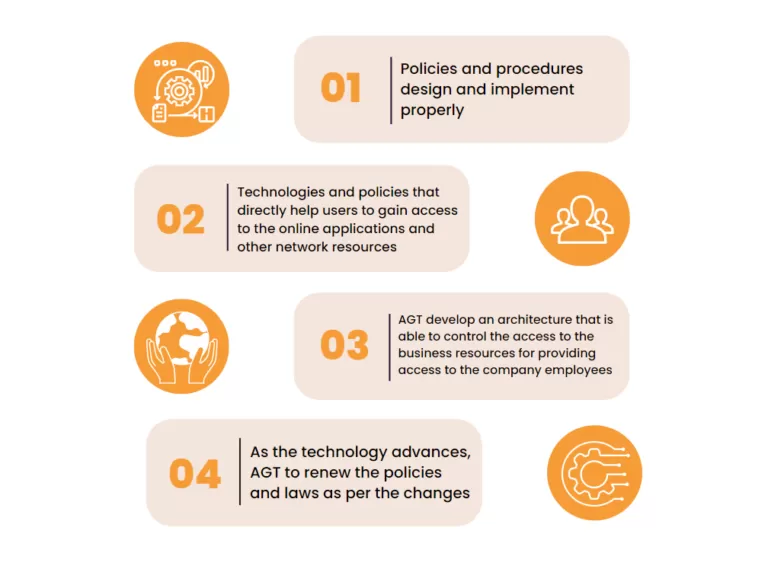
ZERO TRUST SECURITY
Zero Trust is a strategic approach to cybersecurity that secures an organization by eliminating implicit trust and continuously validating every stage of a digital interaction. AGT designed Zero Trust to protect modern environments and enable digital transformation by using strong authentication methods. With digital transformation accelerating in the form of a growing hybrid workforce, continued migration to the cloud, and the transformation of security operations, taking a Zero Trust approach has never been more critical.
BENEFITS
TRUSTED INTERNET CONNECTION
AGT deals with Trusted Internet Connections (TIC) that is a federal cybersecurity initiative intended to enhance network and data security across
the Federal Government.
